I have examined the load reduction performance against brute-force attacks by using IP Location Block. I report the result in this article.
A shell program
The attack.sh is a shell program that measures the load of malicious burst accesses to WordPress back-end such as wp-comments-post.php, xmlrpc.php, wp-login.php, wp-admin/admin-ajax.php using ApacheBench.
It gives an emulation of spam comment, pingback spam, login attempt, and malicious access to the admin-ajax with 5 multiple requests at a time
throughout 60 seconds.
Test environment
I set up the testbed in my local PC which specifications are followings:
| Category | Description |
|---|---|
| Hardware | MacBook Pro / 2.8GHz Core i7 / Memory 16GB |
| Software | OS X 10.9.5 / MAMP 2.0 (Apache 0.2.2.22, PHP 5.4.4) |
| WordPress | 4.3 / Site Language: English |
And here are the plugins installed in the above environments:
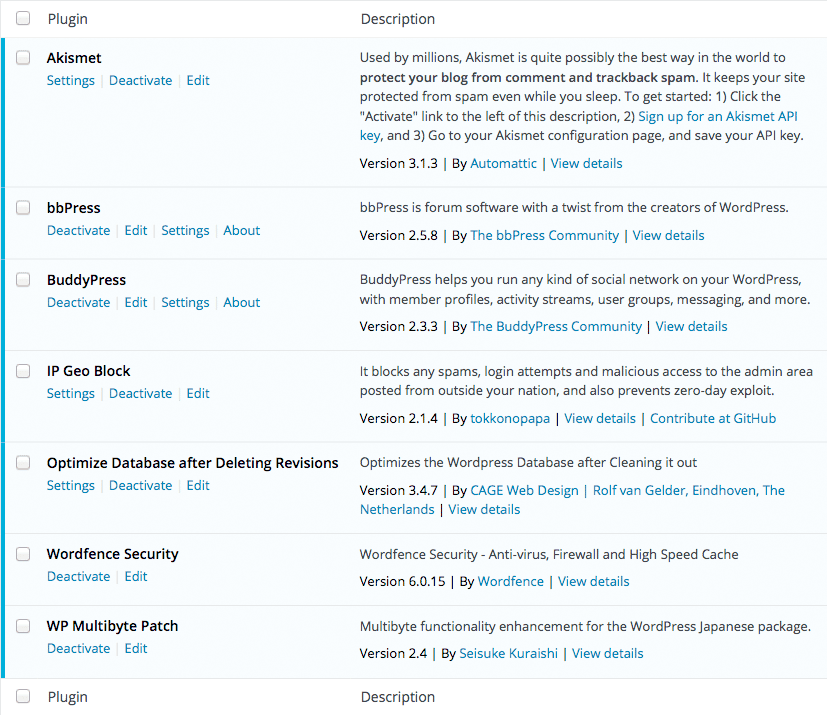
Speaking generally, it is better to separate the hardware on each side of requesting and responding because those have an influence on each other. But unfortunately, I don’t have any such rich environments. So please take it into consideration when you see the results.
Plugins configuration
Wordfence has a lot of options. So I leave them just after installation.
On the other hand, options for IP Location Block 0.2.1.5 are changed as follows:
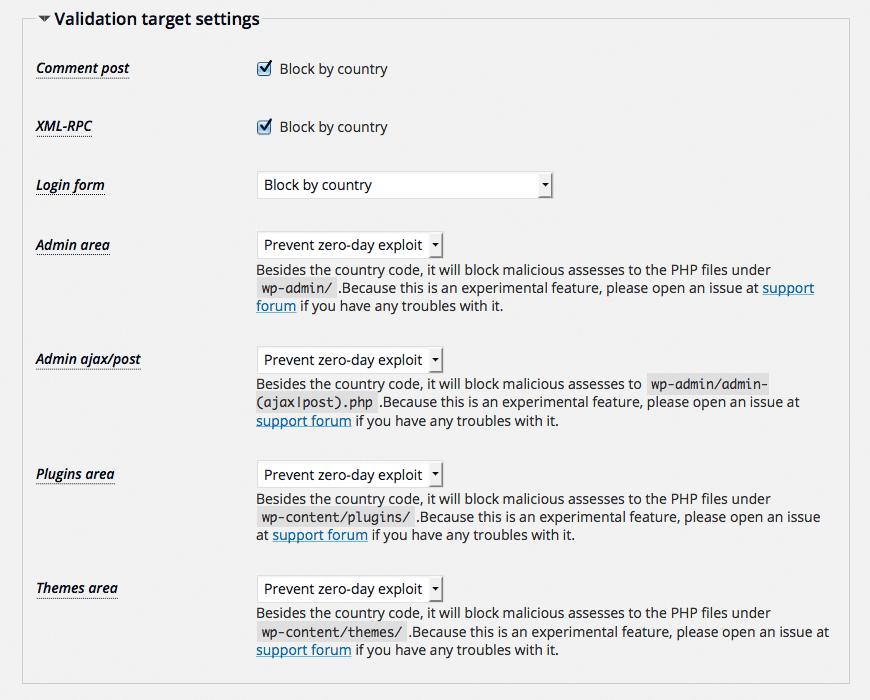
The results
At the beginning of each test, the DB was optimized using Optimize Database after Deleting Revisions.
I picked up only “Requests per second”, “Time per request (across all concurrent requests)” from the results of ApacheBench which indicate the performance of load reduction. The higher in “Requests/sec” and the lower in “Time/req [ms]” are better.
The “IGB” means “IP Location Block”, “WFS” means “Wordfence Security”. And “ON” indicates “Activate” and “OFF” indicates “Deactivate”.
wp-comments-post.php
| IGB | WFS | Requests/sec | Time/req [ms] |
|---|---|---|---|
| OFF | OFF | 4.54 | 220.073 |
| OFF | ON | 4.02 | 248.843 |
| ON | ON | 5.98 | 167.262 |
| ON | OFF | 6.33 | 157.940 |
xmlrpc.php
| IGB | WFS | Requests/sec | Time/req [ms] |
|---|---|---|---|
| OFF | OFF | 6.13 | 163.065 |
| OFF | ON | 5.49 | 182.308 |
| ON | ON | 5.33 | 187.570 |
| ON | OFF | 5.81 | 172.120 |
wp-login.php
| IGB | WFS | Requests/sec | Time/req [ms] |
|---|---|---|---|
| OFF | OFF | 6.43 | 155.479 |
| OFF | ON | 4.97 | 201.078 |
| ON | ON | 5.98 | 167.145 |
| ON | OFF | 6.23 | 160.487 |
When both “IGB” and “WFS” are “ON”, I got the following email:
A user with IP address WWW.XXX.YYY.ZZZ has been locked out from the signing
in or using the password recovery form for the following reason: Exceeded
the maximum number of login failures which is: 20. The last username they
tried to sign in with was: ‘admin’
where “WWW.XXX.YYY.ZZZ” is an IP address which is set by attack.sh. And there are no validation logs in IP Location Block. It means that the execution priority of Wordfence is higher than IP Location Block.
wp-admin/admin-ajax.php
| IGB | WFS | Requests/sec | Time/req [ms] |
|---|---|---|---|
| OFF | OFF | 5.51 | 181.351 |
| OFF | ON | 5.00 | 200.071 |
| ON | ON | 5.53 | 180.822 |
| ON | OFF | 6.03 | 165.840 |
Conclusion
Speaking about the site performance, more plugins leads to less speed. The results show that the performance of load reduction by IP Location Block against brute-force attacks is not so outstanding, but I think it minimizes a rise of the load. 
