RFC1939 defines an autonomous system as follows:
Autonomous system is a connected group of one or more IP addresses run by one or more network operators which has a SINGLE and CLEARLY DEFINED routing policy.
And autonomous system number (ASN) is a registered entity supported by such as Internet Service Providers (ISP) or other large organizations that control blocks of IP addresses.
So we can make use of it to control permissions against the requests instead of using a long list of IP addresses or a ranage of them by CIDR.
New feature: Use AS number
On the “Settings” tab, You can find a new option “Use Autonomous System Number (ASN)” in “Validation rule settings” section. After enabling it, you can specify the AS numbers in the “Whitelist” or “Blacklist” of “extra IP addresses prior to country code” as follows:
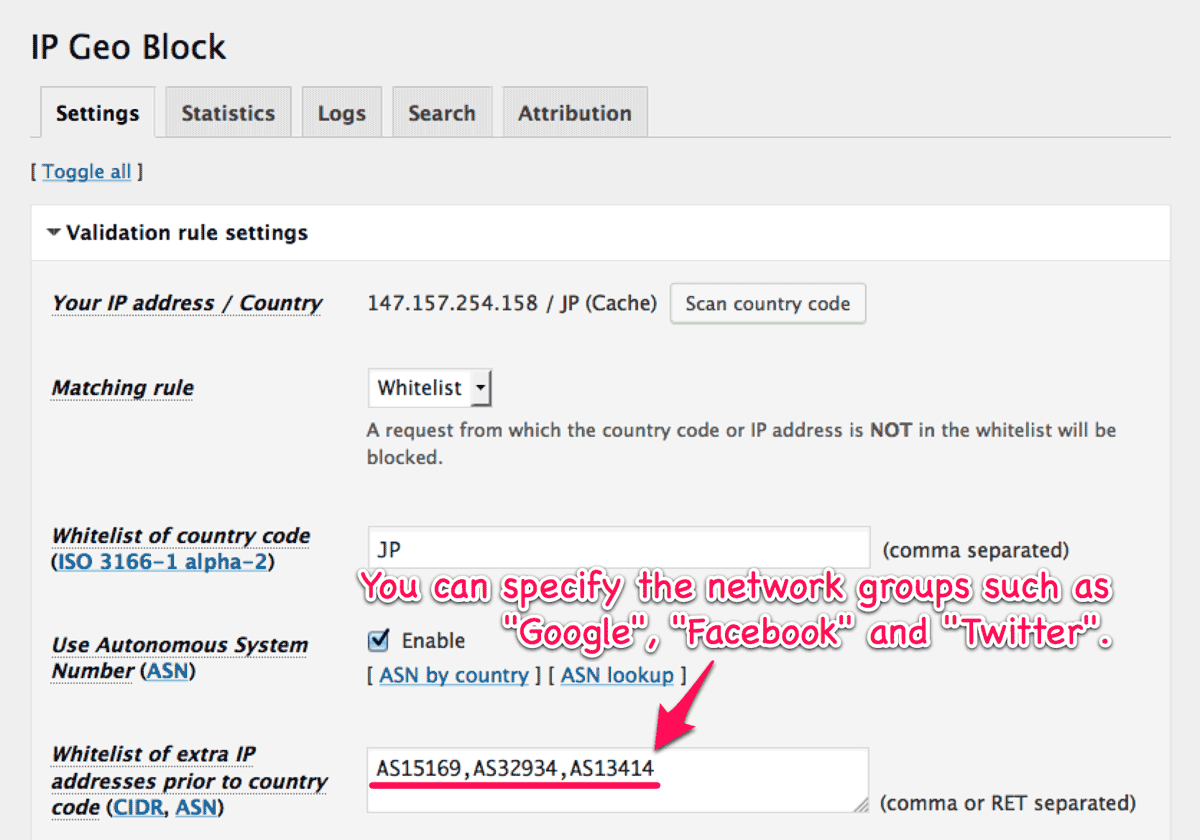
Note that usually ISP, SNS and web search engine provide many services through different network groups. For example, yahoo has registered many AS numbers. So does Google. As for Automattic, Jetpack is run as a service on multiple AS numbers which include other range of IP addresses than Jetpack needs.
Therefore we should notice that an AS number doesn’t always identify the specific organization nor the services. It’s originally aimed for routing IPs to intervene information between different network groups.
On the other hand, this plugin also provides “UA string and Qualification”. For example, Google has many network groups registered as AS15169 which can be put into the “Whitelist of extra IP addresses prior to country code” to accept their bots. Instead of doing this, we can also put Google:HOST into “UA string and Qualification” as their host name can be looked up by its IP address.
So, we need find some good practices to utilize those functionalities.
I would appreciate you if you share what you find  .
.
Server resource usage
This functionality needs additional seeking to dedicated databases. You can check its seek time at “Search tab” when you search an IP address.
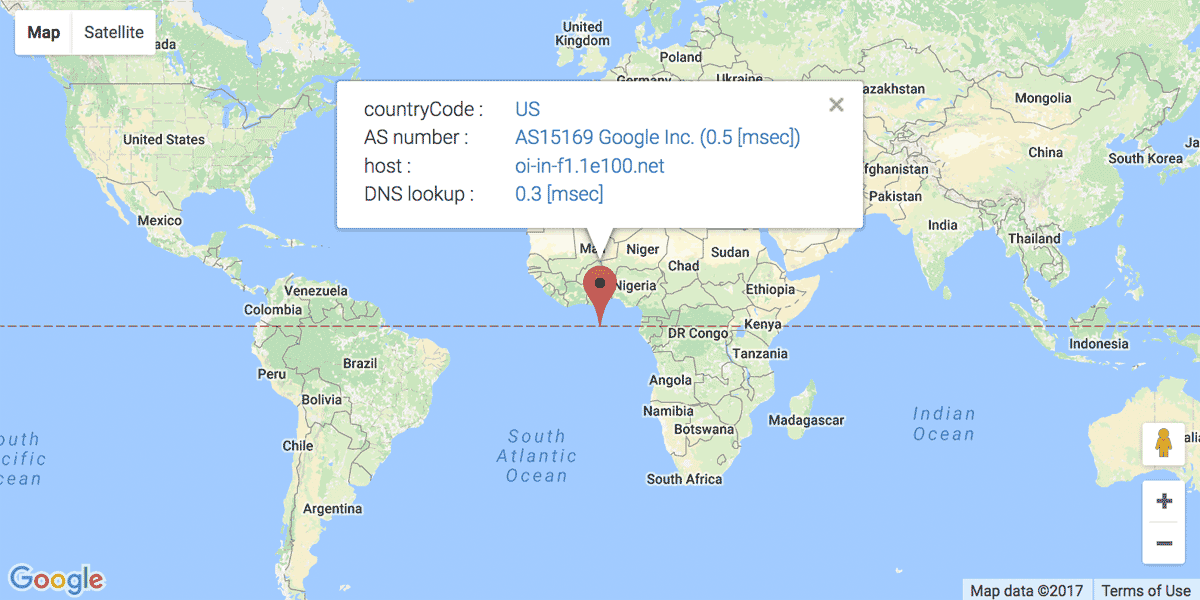
A seeked result would be kept in the cache of IP addresses. So I think it would not be so serious to the site performance. But if you don’t like it, please turn “Enable” off at “Use Autonomous System Number”.
As for size of DBs, its total size for IPv4 and IPv6 would be nearly 10M bytes.
Deleting databases
I’m afraid to say that I didn’t provide you any UI to delete those DBs.
If you do not need those DBs, please delete them directly in “Geolocation API library” folder using FTP or some kind of file manager like cPanel. Then make “Use Autonomous System Number” disabled and perform “Save Changes”.
New feature: Statistics in logs
You might be interested in “WordPress Attack Report” at WordFence blog. Just like this report, you can know what kind of attacks you had in your site.
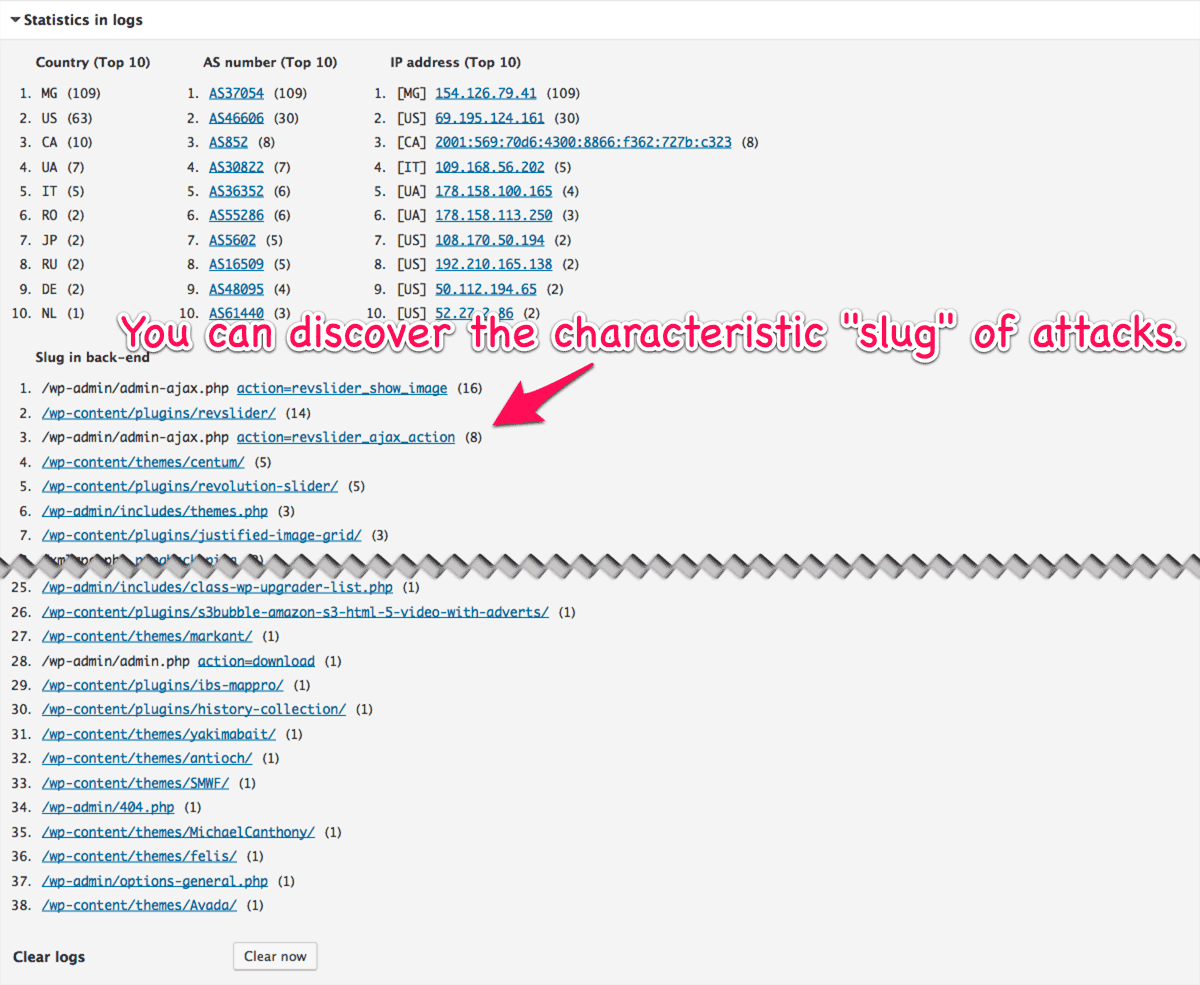
Clicking the links would naviate you to the details on Logs tab.
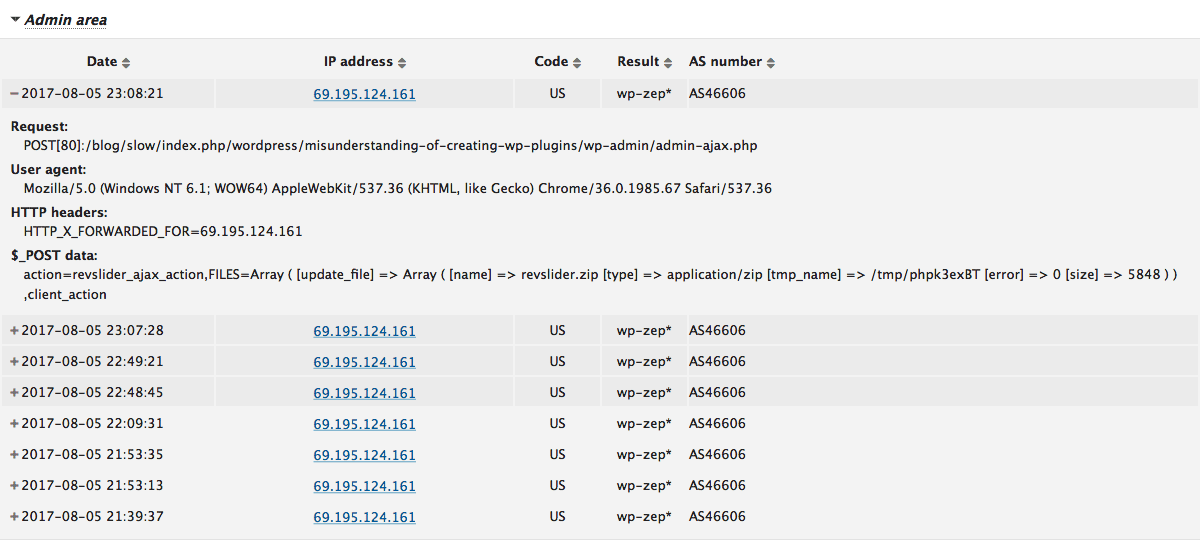
I know I should provide a real time reporting feature in the future. For now, please be patient with this!
Improvement: Capabilities to be verified
This plugin had equipped the protection functionality against Arbitrary File Upload (AFU) since release 0.3.0.3. From this release, you can manage to verify the capability which may be required by a paticular uploader such as Awesome Support plugin.
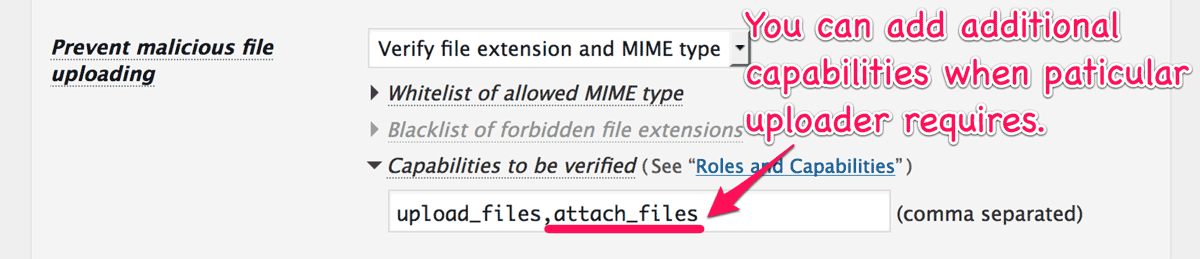
And also add a new filter hook ip-location-block-upload-capability to replace or add the capability to be verified.
Improvement: Compatibility with WP-ZEP
Zero-day Exploit Prevention is one of the strong suit of this plugin. It embeds a special crafted nonce into pages to be protected, and thus effectively blocks malicious access from outside of dashboard.
But based on its mechanism, it is likely to prone to issues. So in this release, I made two improvements.
Inhibit embedding a nonce
Until the previous version, a nonce was embeded into every links independently of the settings for WP-ZEP. From this release, you can manage to inhibit those embedding when WP-ZEP is disabled at each target.
For example, when you disable “Prevent Zero-day Exploit” at “Admin ajax/post”, then no nonce would be embeded into ajax requests.

Candidate actions for exceptions
On your public facing pages, you might want to provide all the services using ajax to each visitor. In this case, you can select “Exceptions” at “Admin ajax/post”.
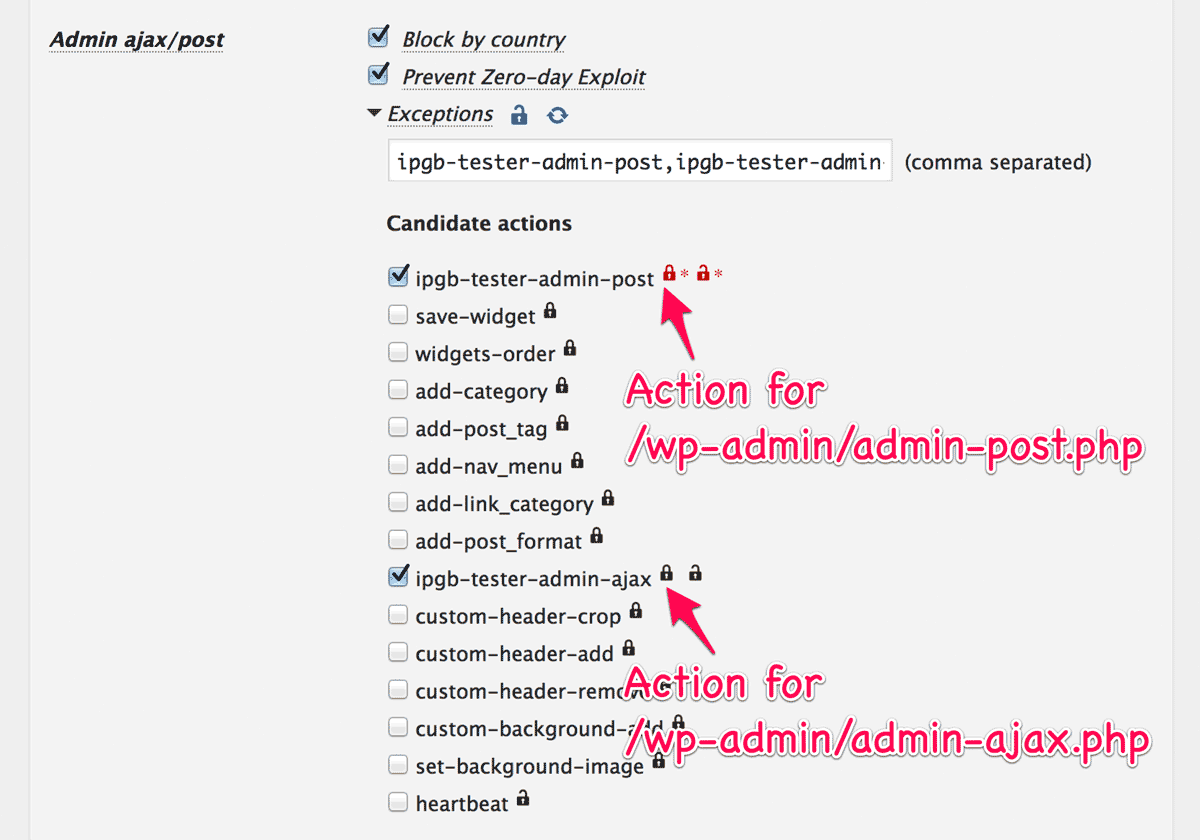
In the previous release, all the actions could not be listed. This issue is fixed in this release. And furthermore, the “unlock icon” (  ) filters actions for non logged-in user on your site so that you can easily pick them up.
) filters actions for non logged-in user on your site so that you can easily pick them up.
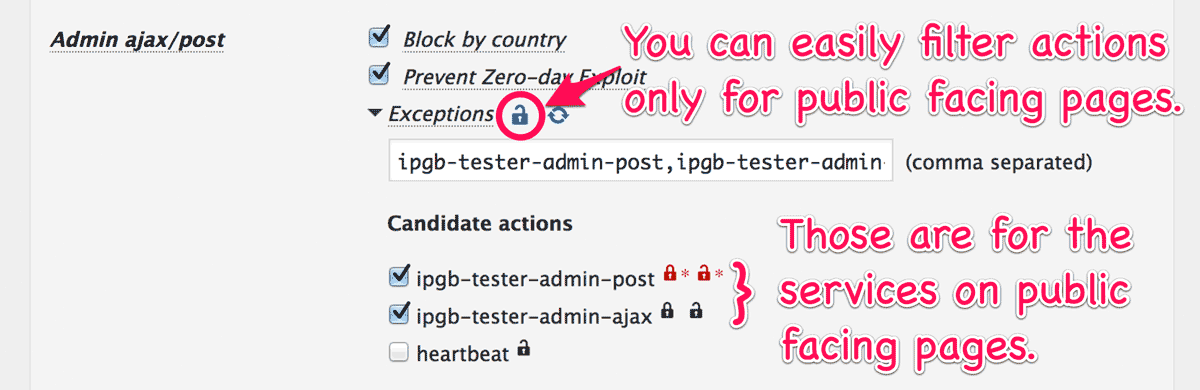
Using these UI, you can easily configure this plugin to block malicious requests against the administrator functions for logged-in users, while you can provide ajax services to all the visitors even from your country.
If you find any issues what I should fix, please let me know at support forum 
