Since the last update of IP Location Block, two plugins were notified of having serious privilege escalation vulnerability. One was WP GDPR Compliance Plugin and another was AMP for WP – Accelerated Mobile Pages.
In this release, IP Location Block has been enhanced to prevent security attacks against this type of vulnerability, based on the principle of “Security by Design”.
New feature: Metadata Exploit Protection
In the past, I analyzed and reported the typical case of privilege escalation vulnerability in WordPress. Both WP GDPR Compliance Plugin and AMP for WP had fell into this trap therefore attackers could modify WordPress database.
The following picture shows the name of action that could be the attack surface on these plugins.
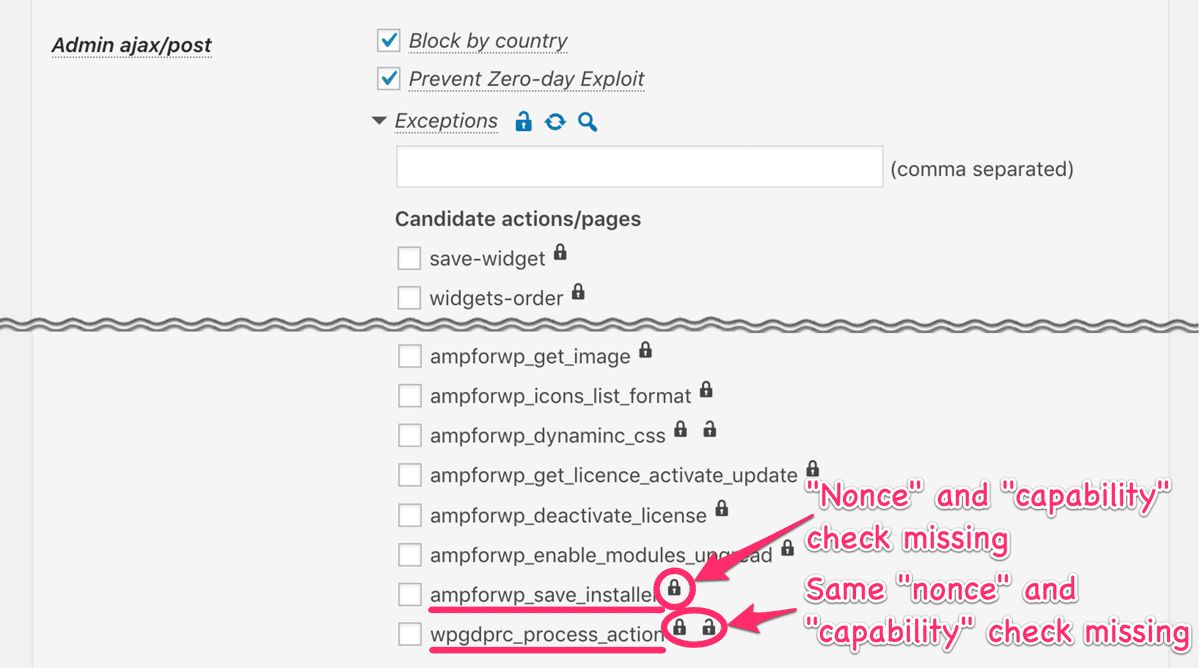
I confirmed that the sites which have the previous version of IP Location Block activated might be protected against those attacks under certain conditions. The former can be blocked by country and the later can be blocked by both country and WP Zero-day Exploit Prevention (WP-ZEP).
From this release, a smart and powerful method named as WP Metadata Exploit Protection (WP-MEP) is added.
How WP-MEP works
Software has to follow the “Security by Design” principle in these days. In a narrow sense, it means considering security as early as the design phase of the software development process. For example, software handles data without exception so that developers have to consider the followings:
- Who access the data with which privilege
- What risk or threat exists if someone access the data without privilege
The most important thing here is that taking these into consideration never depends on attack vectors such as XSS which was the typical flaw of AMP for WP.
WordPress core provides some functions to manage Roles and Capabilities to put the above considerations into practice, but the usage of these completely depends on insecure developers. WP-MEP will manage and protect metadata on behalf of such developers.
Currently, WP-MEP covers {$wpdb->prefix}_options and {$wpdb->prefix}_sitemeta. And you don’t need to enable expressly to activate this feature.
New feature: Network wide settings
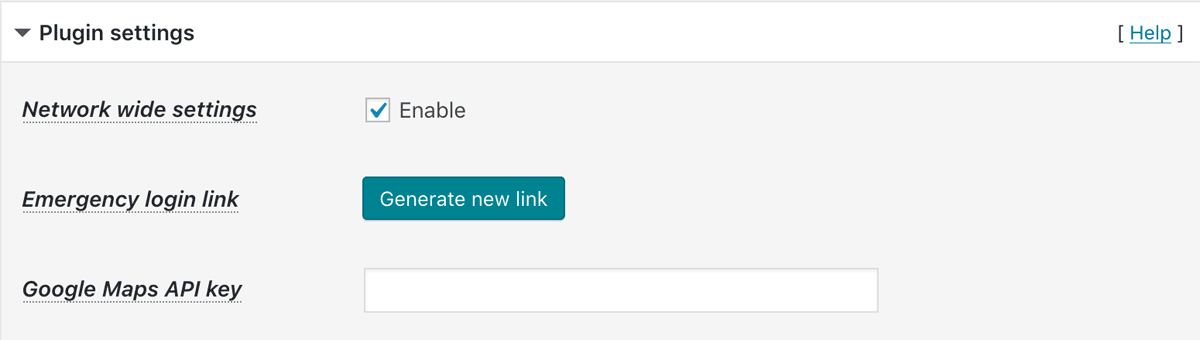
When IP Location Block is network activated on multi-site, you can find “Network wide settings” option in “Plugin settings” section.
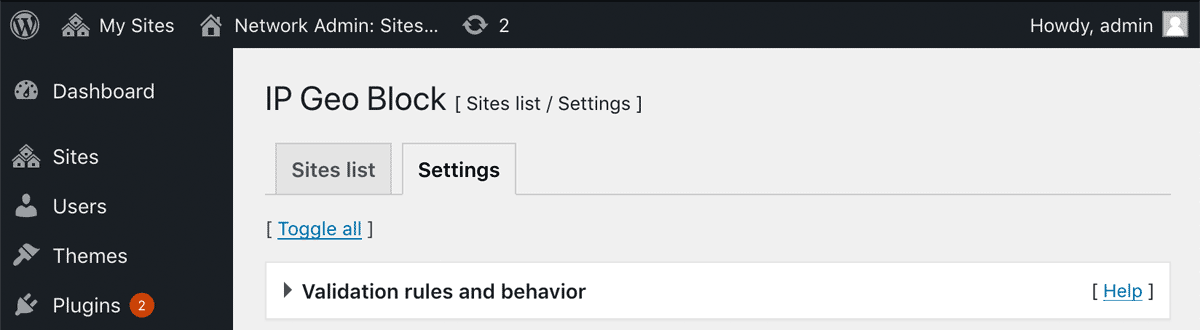
After you enable it, you’ll find “Settings” tab next to “Sites list” on network admin dashboard.
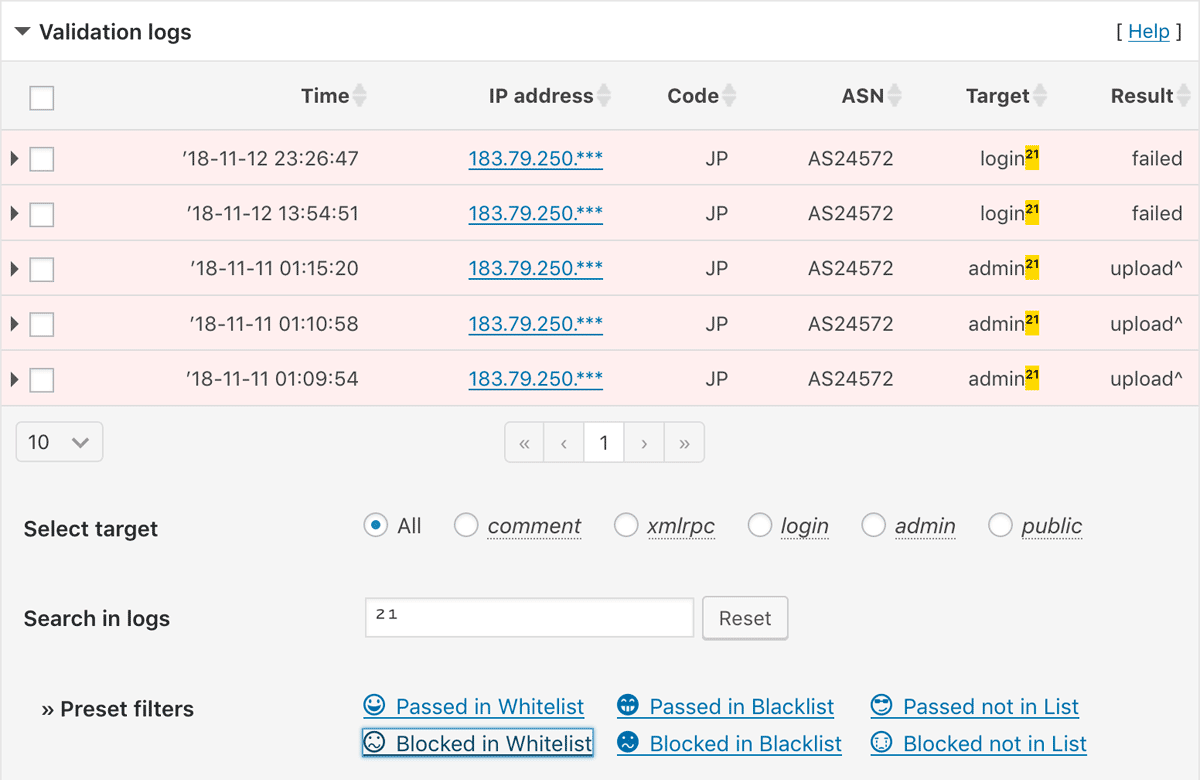
New feature: Preset filters
In version 0.3.0.15, two new filter hooks ip-location-block-logs, ip-location-block-logs-preset which can filter the specific log entries for ease of analysis were added. This feature was based on the awesome proposal in the forum topic by Tony G.
I found it was very useful in order to identify which requests should be passed or blocked. So I introduced this feature as a regular functionality as follows:
TL;DR: The description of this plugin
I updated the description of this plugin on WP.org as follows:
The more you install themes and plugins, the more likely your sites will be vulnerable, even if you securely harden your sites.
While WordPress.org provides excellent resources, themes and plugins may often get vulnerable due to developers’ human factors such as lack of security awareness, misuse and disuse of the best practices in those resources.
This plugin focuses on insights into such developers’ human factors instead of detecting the specific attack vectors after they were disclosed. This brings a smart and powerful methods named as “WP Zero-day Exploit Prevention” and “WP Metadata Exploit Protection”.
Combined with those methods and IP address geolocation, you’ll be surprised to find a bunch of malicious or undesirable access blocked in the logs of this plugin after several days of installation.
I’m very proud of IP Location Block as it’s the only plugin which has the approach from human factors’ point of view among security plugins ever released so far.
Have fun! 
