The legal framework for protection of personal data in EU will be changed from Directive 95/46/EC to General Data Protection Regulation (GDPR) that will come into force on 25 May 2018.
It was a big challenge for me to make my plugin complied with this regulation, because this plugin records IP address which is considered as personal data into its logs and cache on the database.
The main topic of this release note is to describe how this plugin was changed to meet the GDPR compliance.
Legitimate interest
It goes without saying that analysis of access log is important for security. Apart from being able to directly or automatically identify the malice of the requested data, the footprints in the log can help not only to identify the security breach but also to manually analyze malicious intention and to block such requests.
While GDPR requires explicit consent of “Data Subject” for sensitive personal data or unambiguous consent for non-sensitive data, getting consent to record access log before responding does not make sense especially when attackers use some tool to compromise the website.
GDPR states about such a case as “Legitimate interest” for specific purpose of processing. GDPREU.org says:
Beyond Recital 47 stating that fraud prevention “constitutes a legitimate interest”, Recital 49 states that the necessary and proportionate processing for network security “constitutes a legitimate interest”
The Recital 49 states:
The processing of personal data to the extent strictly necessary and proportionate for the purposes of ensuring network and information security
Of course, recording access log should not override fundamental rights and freedoms of the data subject stated in “Lawfulness of processing” as follows:
(f) processing is necessary for the purposes of the legitimate interests pursued by the controller or by a third party, except where such interests are overridden by the interests or fundamental rights and freedoms of the data subject which require protection of personal data, in particular where the data subject is a child.
Therefore, I had to consider technical and functional requirements to meet GDPR compliance.
Technical requirements for GDPR
GDPREU.org summarizes the aim of GDPR and data subject rights to protect all EU citizens from privacy and data breaches as follows:
- Breach Notification
- Right to Access
- Right to be Forgotten
- Data Portability
- Privacy by Design
- Data Protection Officers
I think the first right and the last one would not be related to the blocking functionality of this plugin. And for the rest of the rights, I have taken my interpretation down into the functions of this plugin as follows:
- Privacy and record settings
All the settings related to personal data processing are now managed in Privacy and record settings section. If you do not want to record any IP addresses, you can disable Record Statistics, Record Logs and Record IP address cache to definitely comply with GDPR.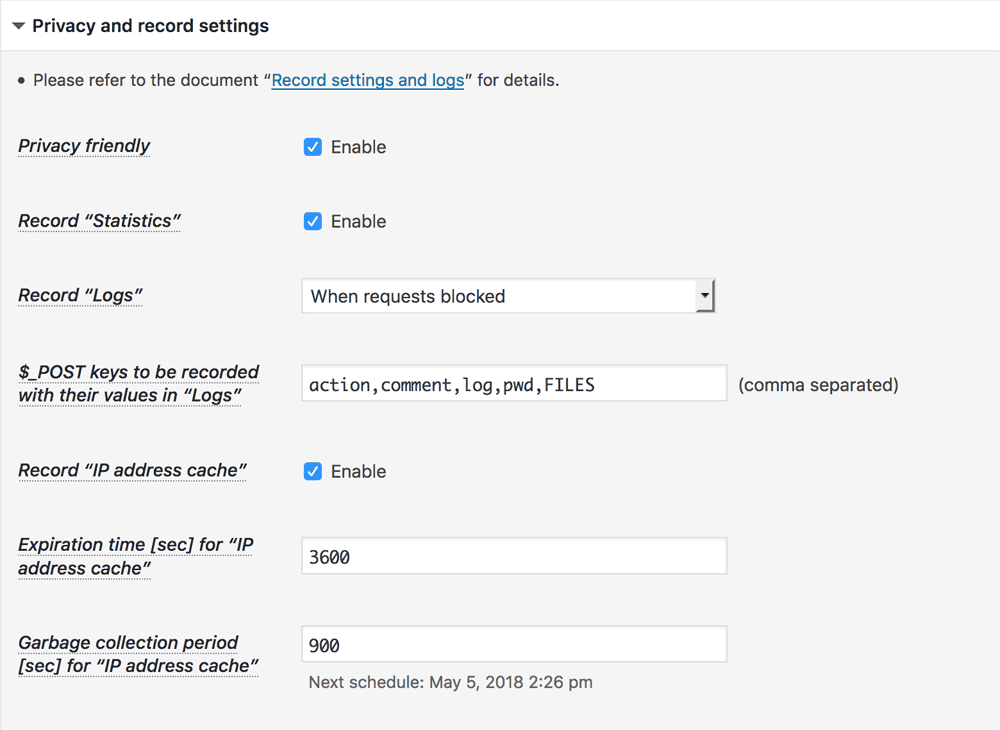 Note: When Record IP address cache is disabled, limiting login attempts can not work.
Note: When Record IP address cache is disabled, limiting login attempts can not work. - Manage 3rd parties’ API
When you enable the option Privacy friendly, only the local geolocation databases are used to get country code from IP address to prevent sending sensitive data to the 3rd parties’ API via HTTP.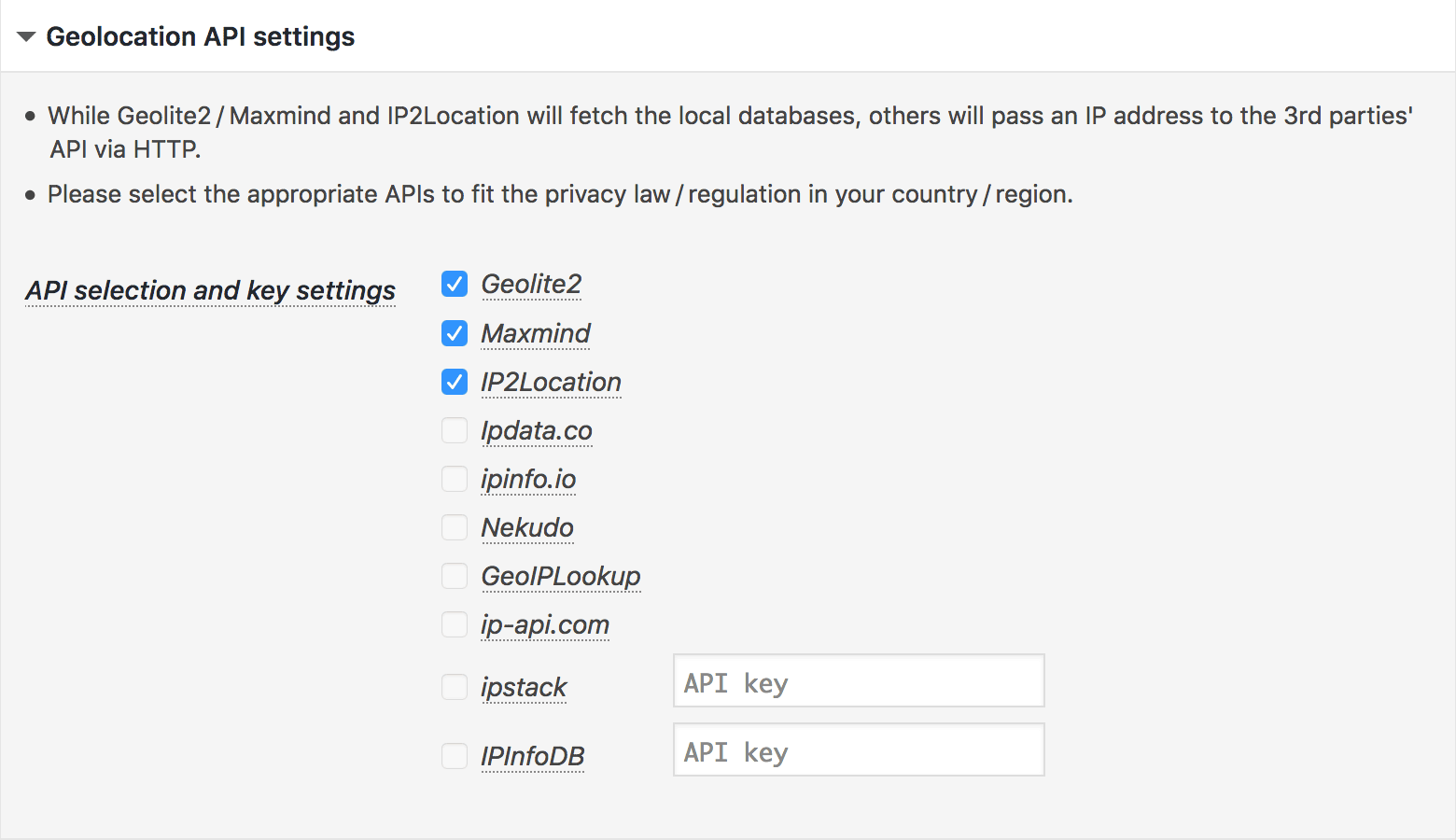
- Anonymize IP address
In GDPR, this function is related to “Pseudonymisation” which is the processing of personal data such that it can no longer be attributed to a single data subject without the use of additional data, so long as said additional data stays separate to ensure non-attribution.This function is for Privacy by Design in GDPR. When the option Privacy friendly is enabled, IP address in logs / cache is anonymized with three asterisks
***.
Even when Privacy friendly is enabled, you can access the 3rd parties’ API on Search IP address geolocation, but the last number of specified IP address will be replaced to
0like123.456.789.0to prevent inadvertent sending personal data to the 3rd parties .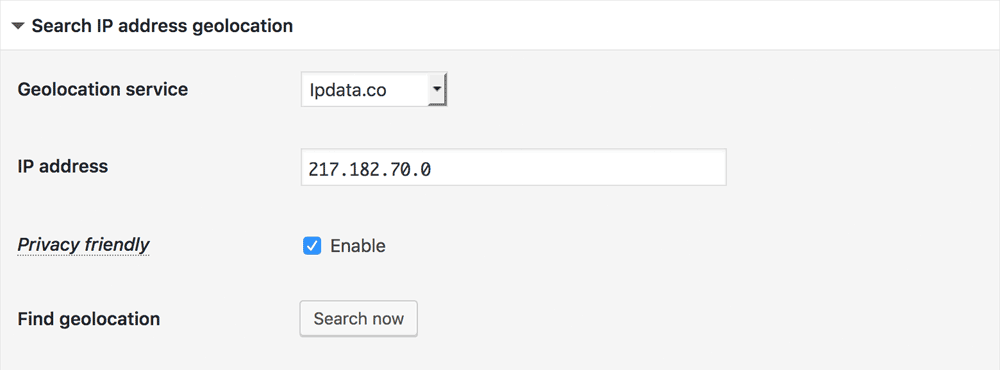
- Encrypt IP address
IP address in logs / cache is now always encrypted by AES to prepare for personal data breach. This is also for Privacy by Design.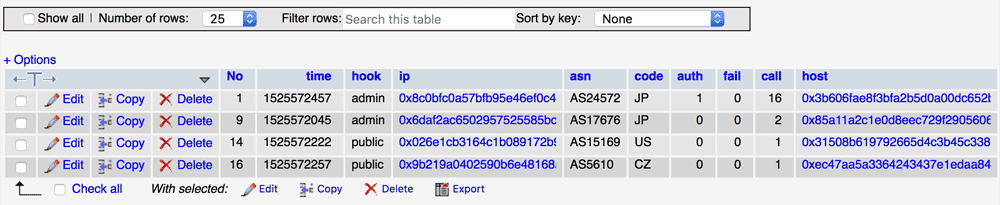
- Remove entries by IP address
This is related to Right to Access and Right to be Forgotten.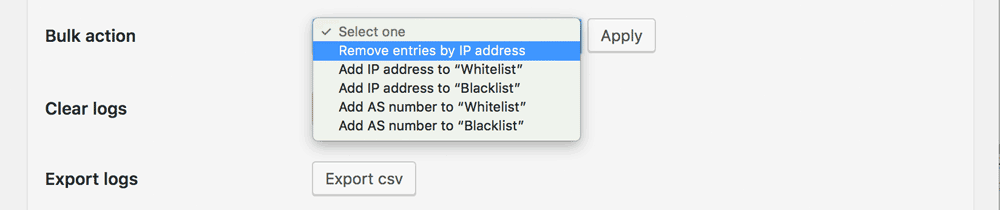
- Export logs by csv
This function is for logs / cache and just for Right to Access and Data Portability. - Log rotation
Log rotation is an automated processing that erases outdated data which seems to be related to Right to be Forgotten. The entries in logs and cache in this plugin will be removed when exceeded a certain amount / time.
Thought about the balance
Needless to say that all website administrators need to monitor, detect, protect and respond to the security matters such as intrusion, hacking, hijacking, data breaches and so on, to protect property of stakeholders including website visitors and customers. And also I believe personal data should be protected as GDPR requires  .
.
To achieve both of them, the balance between them is most important. So for those purpose, I wish I could provide some technological solution to contribute to WordPress community.
Of course I’m not a lawyer nor a jurist  as I stated at the beginning of this article. So any advices and discussions will be appreciated
as I stated at the beginning of this article. So any advices and discussions will be appreciated  .
.
Reference
Update of Geolocation APIs
freegeoip.net make a fresh start as ipstack.com and it needs API key available “Get Free API Key” to use even for free.
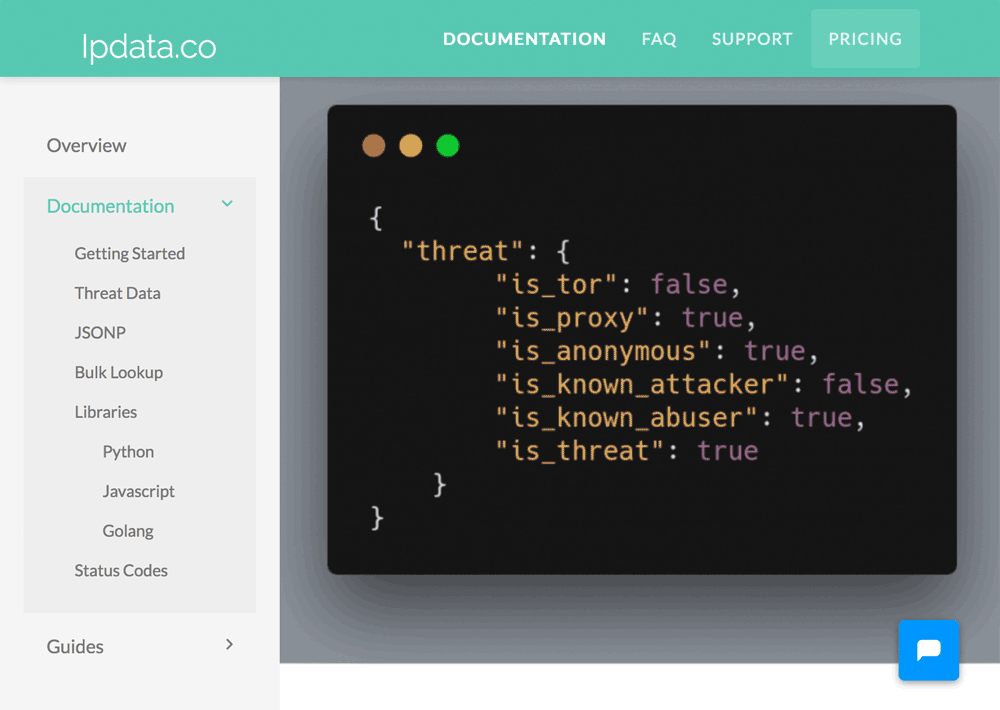
Another API by Xhanch was dropped because it supports only IPv4. Instead of this, a new comer Ipdata.co is now introduced. You can make upto 1500 requests daily via HTTPS for free. And the most unique feature is “Threat intelligence Data” that can identify 600M malicious IP addresses, open proxies, tor nodes, spammers, botnets, attackers and so on.