In this release, the ability of WP-ZEP have been greatly improved. Previously, the probability of successful prevention against the zero-day attack (true positive) was estimated about 26%. But now it’s 60%. Please refer to this article about the background of these percentage.
In this note, I’ll mention what’s new in 0.2.1.0.
New feature
In 0.2.0.8 or less, the prevention target of WP-ZEP was as follows:
wp-admin/admin-ajax.phpandwp-admin/admin-post.phpwithactionwp-admin/admin.phpwithaction
In 0.2.1.0, the followings are added:
wp-admin/*.phpwithpagewp-content/plugins/name-of-plugin/…/*.phpwp-content/themes/name-of-theme/…/*.php
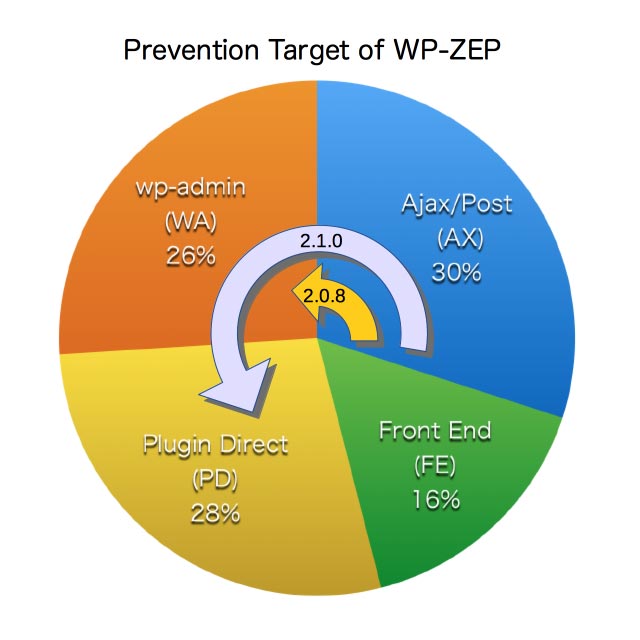
Along with these expansions, two filter hooks ip-location-block-admin-pages and ip-location-block-wp-content can be available to specify some pages or plugins to drop them from the target. To use those filter hooks, you should add appropriate code into your functions.php as follows:
<?php
add_filter( 'ip-location-block-admin-pages', 'my_admin_pages' );
add_filter( 'ip-location-block-wp-content', 'my_wp_content' );
function my_admin_pages( $names ) {
// ex) wp-admin/tools.php?page=name-of-page
return $names + array( 'name-of-page' );
}
function my_wp_content( $names ) {
// ex) wp-content/plugins/name-of-plugin/
// ex) wp-content/themes/name-of-theme/
return $names + array( 'name-of-plugin', 'name-of-theme' );
}
?>I hope there’s no need this kind of bypass. 
Bug fix
There’s a bug that the order of the arguments for the action handler ip-location-block-backup-dir was incorrect. Now it works correctly as shown in the samples.php.
Bug fix
In WordPress 4.2, MySQL tables had been upgraded to utf8mb4 if it is available. If the charset of the table is utf8 and there’s 4 bytes character in the record, $wpdb->query() will fail to insert it into db.
Because utf8mb4 is available only on MySQL 5.5.3 or higher, I’ve decided to keep utf8 for the charset of validation logs. So I added the script which eliminate 4 byte character from the record.
Improvement
In the previous version, the “Referrer Suppressor”, that eliminate the browser’s referer, do nothing with an element which is added into the DOM after DOM ready. This issue could be seen at the “WordPress News” on the dashboard, where the contents were added after firing the browser’s document ready.
It doesn’t mean that this plugin was vulnerable but should be fixed. The click event handler is now delegated at the body.
