When I go abroad, I want to manage my WordPress site as an administrator from there. To realize this, I’ve implemented a new feature which was proposed at the support forum. (Thanks, digiblogger !!)
A new feature for login
A new choice Block by country (register, lost password) has been equipped at “Login form” on “Settings” tab. This feature allows you to “login” and “logout” from anywhere, but any other request to login form will be validated by the country code.
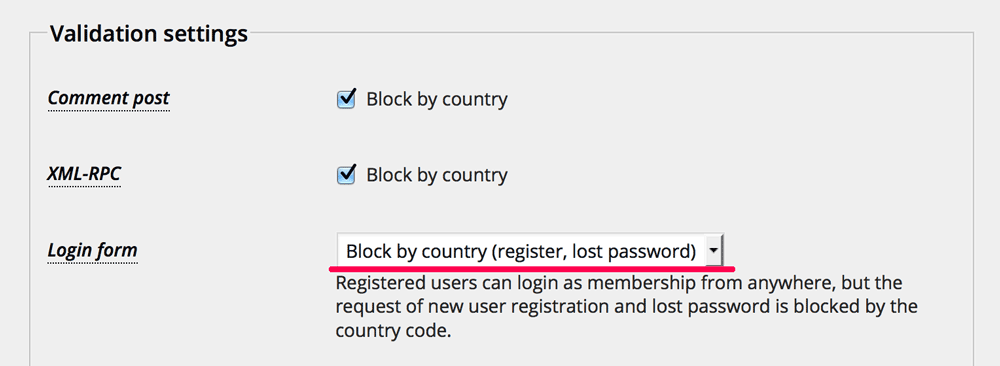
It’s suitable for “Membership: Anyone can register” on “Settings General Screen”. Also for BuddPress and bbPress.
One thing you should know about this feature is that it changes the priority of validation rules. Basically, this plugin has 3 rules, i.e. WP-ZEP, country code and authentication. In the previous version, the priority of those are as follows (“BBC” means “Block by country”):
| Login form | 1st priority | 2nd priority | 3rd priofity |
|---|---|---|---|
BBC |
WP-ZEP | country code | authentication |
In this version:
| Login form | 1st priority | 2nd priority | 3rd priofity |
|---|---|---|---|
BBC |
WP-ZEP | country code | authentication |
BBC (...) |
WP-ZEP | authentication | country code |
The reason why the BBC (...) has different priority from BBC is that I would not like to change the priority of the previous version. So you have nothing to do if you would not use this feature.
If you choose it and want to add more permitted countries for login, you can embed the following codes into your functions.php:
<?php
function my_whitelist( $validate ) {
$whitelist = array(
'JP', 'US', // should be upper case
);
$validate['result'] = 'blocked';
if ( in_array( $validate['code'], $whitelist ) )
$validate['result'] = 'passed';
return $validate;
}
add_filter( 'ip-location-block-login', 'my_whitelist' );
?>A new feature for bbPress
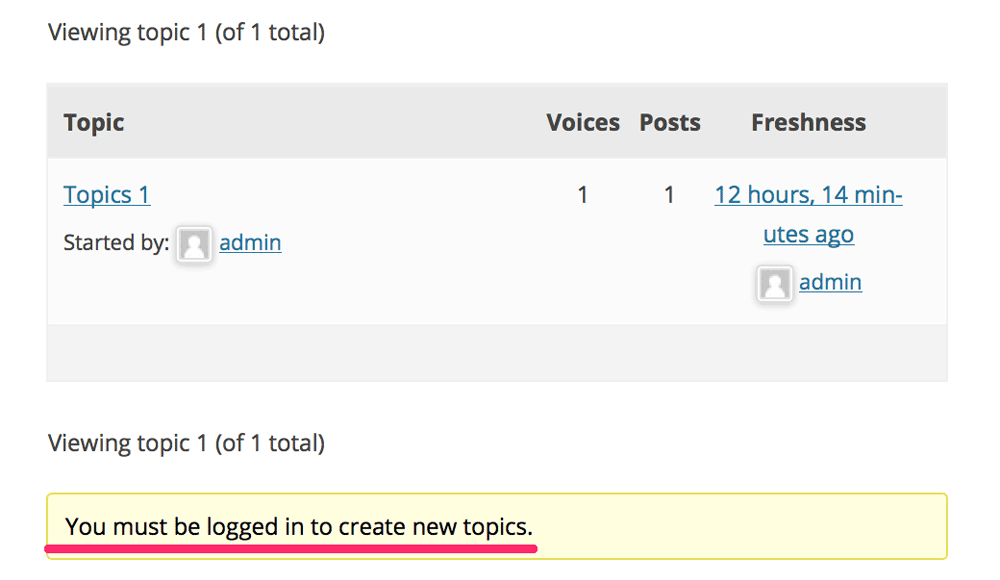
If you choose Block by country at “Comment post” on “Settings” tab, a user can’t post data to create a new topic and reply (where the http response is “403 Forbidden” by default) unless he/she is logged in.
With the combination of the previous feature, this can help to reduce spams.
To test this feature, add the following codes into your functions.php (of course on your test site  ).
).
<?php
function my_replace_ip( $ip ) {
return '98.139.183.24'; // yahoo.com
}
add_filter( 'ip-location-block-ip-addr', 'my_replace_ip' );
?>A drawback of this feature is that the convenient behavior of bbPress will be disabled. When you log out and log in again, bbPress takes you to the page where you were. As this could be potentially block you, this plugin behaves same as BuddyPress when your log out.
A new feature for an error page
For example, the 403.php in the theme template directory or child theme directory is used (if it exists) when this plugin blocks specific requests.
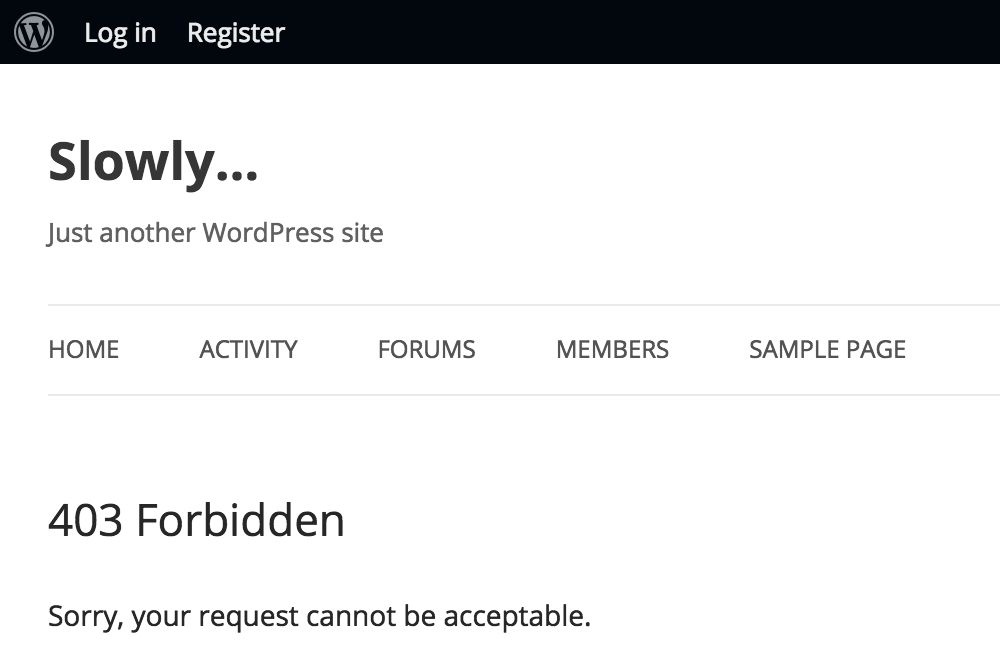
And also some new filter hooks are available to customize the http response status code and reason message:
ip-location-block-comment-status,ip-location-block-comment-reasonip-location-block-xmlrpc-status,ip-location-block-xmlrpc-reasonip-location-block-login-status,ip-location-block-login-reasonip-location-block-admin-status,ip-location-block-admin-reason
Use those hooks as follows:
<?php
function my_login_status( $code ) {
return 503;
}
function my_login_reason( $msg ) {
return "Sorry, this service is unavailable.";
}
add_filter( 'ip-location-block-login-status', 'my_login_status' );
add_filter( 'ip-location-block-login-reason', 'my_login_reason' );
?>Obsoleted filter hooks
With some improvement of internal logic, ip-location-block-(admin-actions|admin-pages|wp-content) were obsoluted. Alternatively new filter hooks ip-location-block-bypass-(admins|plugins|themes) are added to bypass WP-ZEP.
As long as there is no trouble with WP-ZIP, this feature would not be necessary. But if you need, please check out samples.php about the usage of these hooks.
Capturing malicious access to the plugins/themes
Some silly attackers (or tools) send invalid requests to the plugins/themes area whose path are like this:
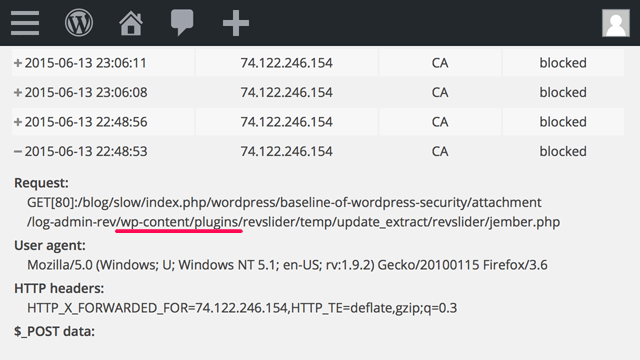
This kind of access seems to be aimed at the contaminated sites. Normally it fails in “404 Not Found” and don’t matter even when we leave them alone. However, I think it’s a good chance to know the malicious post pattern if this plugin records such a footprint. So I made the condition of capturing a malicious access to the plugins or themes area in a loose manner.
Although it’s a little annoying, please be patient and enjyo this release !! 
