WordPress has many important backend entrances (i.e. endpoint) that will affect on the website. In this section, you can set up rules to validate requests for particularly important endpoints among them.
Comment post
It validates requests to wp-comments-post.php.
- Message on comment form
You can put the specified message at the point where template action hookcomment_formorcomment_form_topis fired. The following tags are allowed:<a>,<abbr>,<acronym>,<b>,<cite>,<code>,<del>,<em>,<i>,<q>,<s>,<strike>,<strong>
XML-RPC
It validates requests to xmlrpc.php.
The plugin Jetpack by WordPress.com will access this endpoint from their servers in United States. Therefore, cooperation with WordPress.com does not work if the country code US is not in “Whitelist of country code” or not in the blacklist.
In such a case, please put IP addresses of Jetpack servers or the AS number AS2635 of Automattic, Inc into “Whitelist of extra IP addresses prior to country code”.
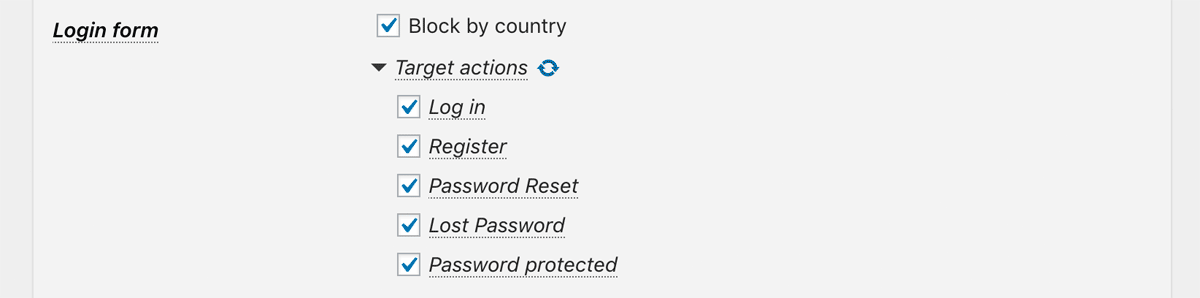
Login form
It validates requests to wp-login.php and wp-signup.php.
- Target actions
In addition to login, you can enable actions such as user registration, password protected page and so on.
- Max number of failed login attempts per IP address
Select the maximum number of possible login attempts. “Record “IP address cache”” should be enabled in “Privacy and record settings” section.
Admin area
It validates requests to wp-admin/*.php.
Requests to this area would cause a redirection to the login page or unintentional affects on the website due to attacks that exploit vulnerabilities in themes and plugins (in case of being authenticated).
- Prevent Zero-day Exploit
You can protect your site from these attacks that can not be prevented with “Block by country”.
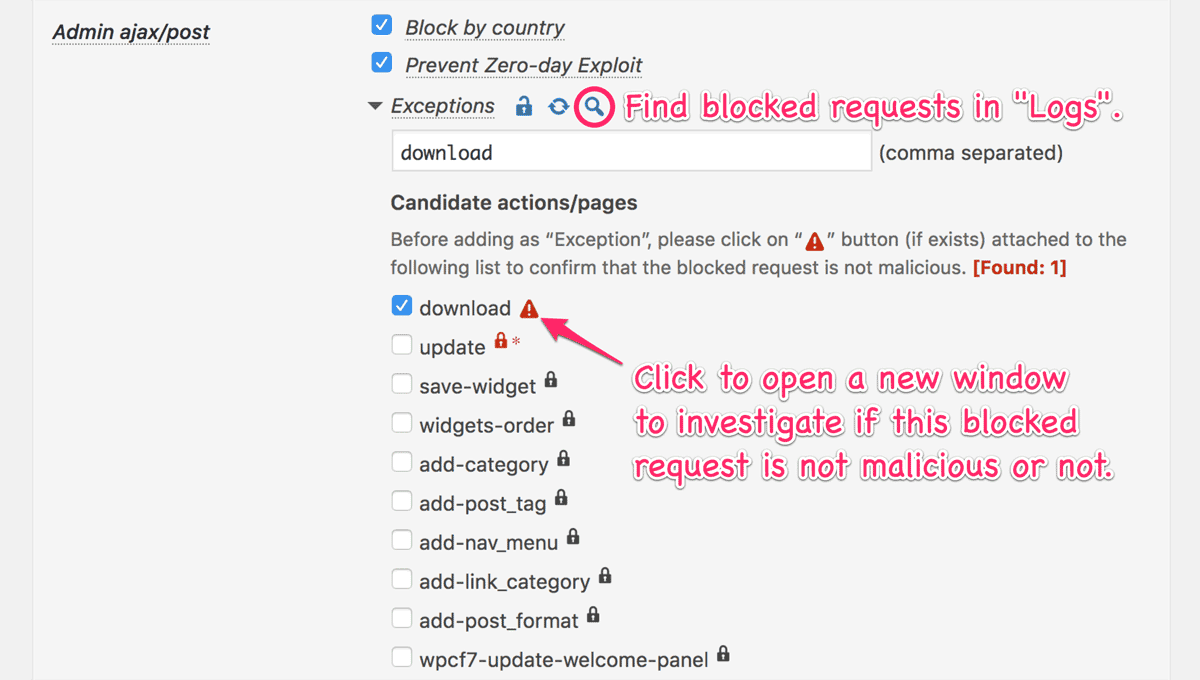
Admin ajax/post
It validates requests especially to wp-admin/admin-ajax.php and wp-admin/admin-post.php.
These endpoints are used as WordPress standard interfaces for themes and plugins to perform their specific tasks. But many vulnerable themes and plugins were out there due to lack of secure coding to use these endpoints.
-
Prevent Zero-day Exploit
You can protect your site from attacks targeted at those vulnerabilities that can not be prevented with “Block by country”. -
Exceptions
When “Prevent Zero-day Exploit” is enabled, unintentional blocking may occur depending on a theme or plugin. In such a case, please select the corresponded action / page in the list. You can easily find such blocking using a magnifying glass button ( ) then an alert button (
) then an alert button (  ) can navigate you to the Logs tab to closely look up such blocking.
) can navigate you to the Logs tab to closely look up such blocking.Special care must be taken when you specify actions with only a lock icon (
 ) as exceptions, because those actions are for administrator only.
) as exceptions, because those actions are for administrator only.
Plugins area
It validates requests to wp-content/plugins/⋯/*.php.
-
Prevent Zero-day Exploit
Many vulnerabilities are found in plugins that are programmed to call PHP directly under their own directly. This option protects the site against attacks against these vulnerabilities that can not be prevented by “Blocking by country” alone. -
Force to load WP core
Like TimThumb, there are certain types of plugins which have PHP files that can be called independently of WordPress. This ends not to perform validation by this plugin. For such cases, this option can protect the site that can not be prevented by “Blocking by country”. -
Exception
It is almost the same as “Admin ajax/post”, but plugin name should be specified.
Themes area
It validates requests to wp-content/themes/⋯/*.php.
“Force to load WP core” and “Exception” are almost the same as “Plugins area”.
