Sucuri published “Website Hacked Trend Report” and reported that backdoor and malware are the top 2 of infection trends in Q1 2016.
How attackers get websites hacked?
The following chart (sorry but it is based on the data in Apr. 2015) suggests that vulnerabilities in plugins are the top source of WordPress websites being exploited. It also shows that Arbitrary File Upload which may directly cause websites hacked is the 3rd place among all the type of threats.
Now, I’m very pleased to announce that IP Location Block 0.3.0.3 has an ability to prevent those type of threats!!
Arbitrary File Upload
You can find a bunch of AFU in WPScan Vulnerability Database. Most cases utilized /wp-admin/admin-ajax.php as an entry point of malicious uploading. Some of them could be blocked by “Zero-day Exploit Prevention” but some of them could not in the previous version.
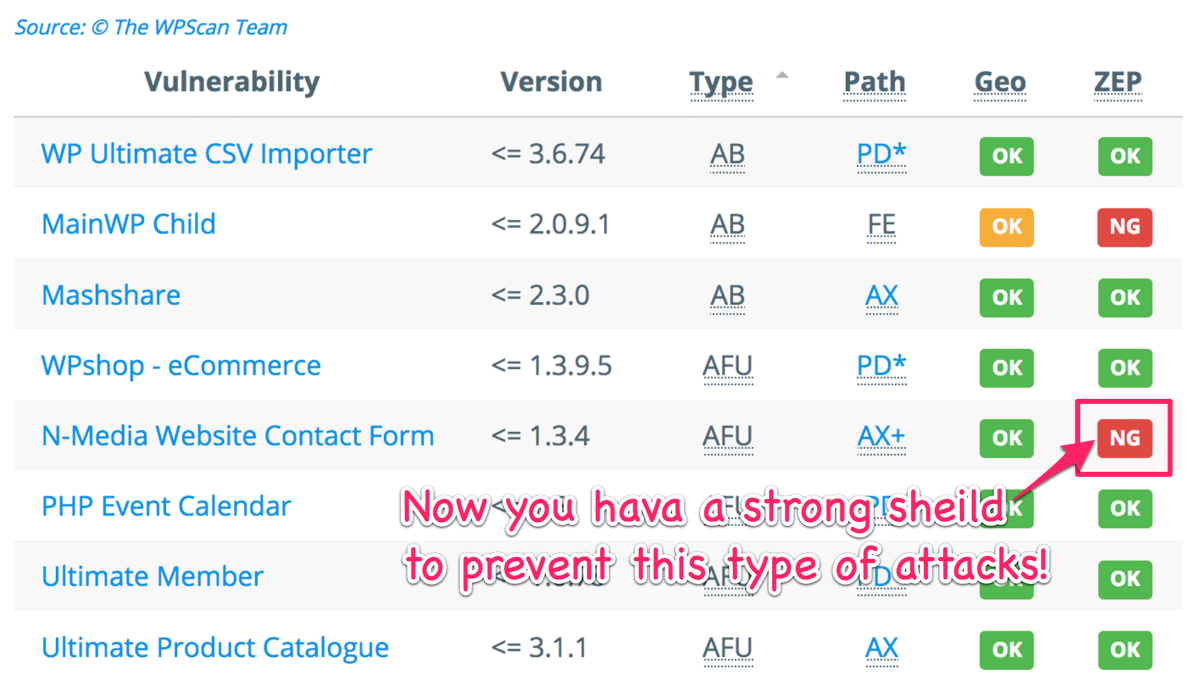
For example, the following table reported in the past indicates that WP-ZEP could not block AFU if a plugin would provid its service for both logged-in user ( ![]() ) and not-logged-in user (
) and not-logged-in user ( ![]() ).
).
But now, you’re safe against this type of attacks!
New feature: Prevent malicious upload
By default, WordPress accepts the following file types (or extension) so that a logged-in user can upload them on dashboard.
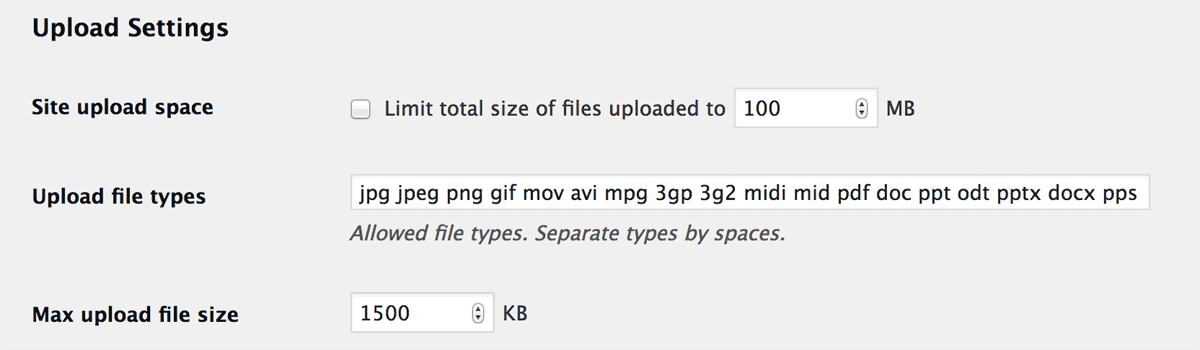
But some plugins or themes that provide uploading functionality may accept different file types from those which WordPress accepts. And sometimes they would fail to verify the file types or loose to verify user’s capability.
So “Verify capability and MIME type” will validate the both MIME type and file extension and also user capability on behalf of those vulnerable plugins and themes.
Now you can find a new option “Prevent malicious upload” in “Validation rule settings” section. It enables to verify the capability (i.e. upload_files) and restrict the MIME types of uploading files.
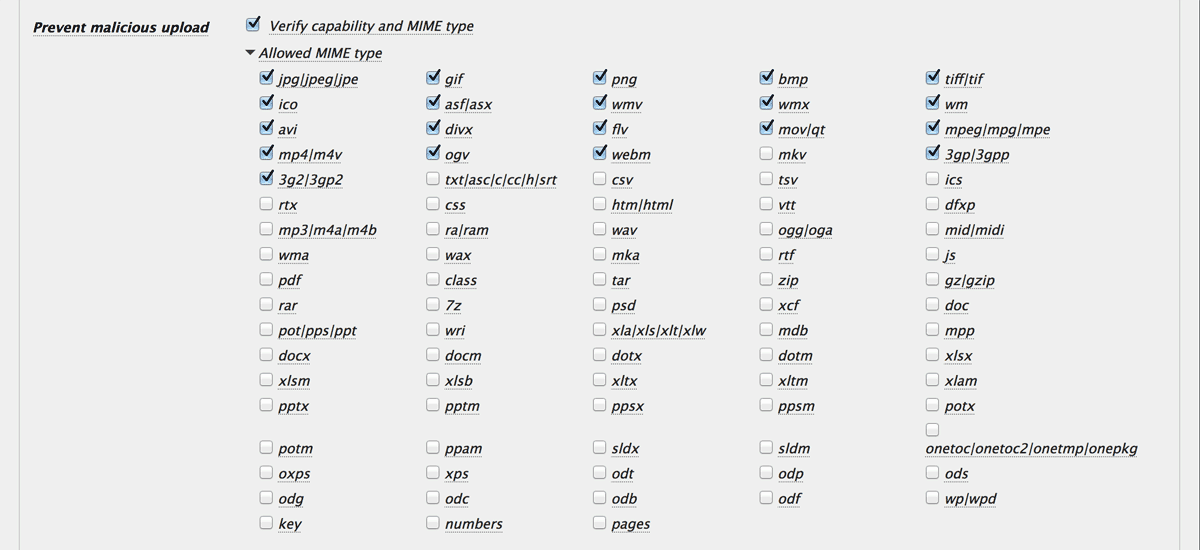
If this configuration is too strong for your demand, “Verify only file extension” is your 2nd choice.
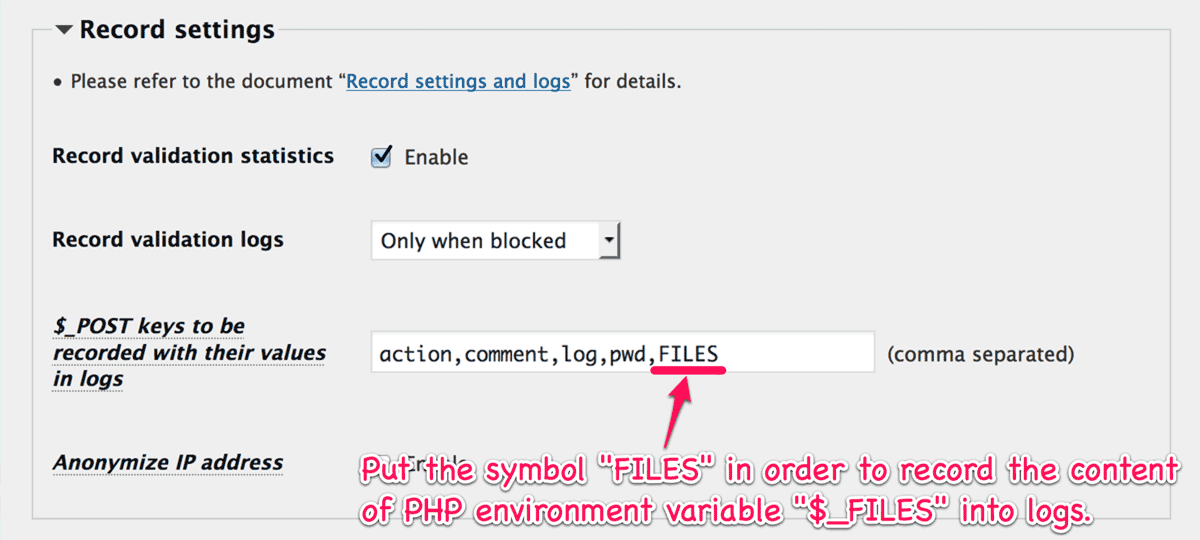
After you enable this feature, you may be supprised to find some malicious uploading in the logs within a few days. The following picutre shows that the attackers attempted to upload zip file including malware targeted at vulnerability of Revolution Slider.
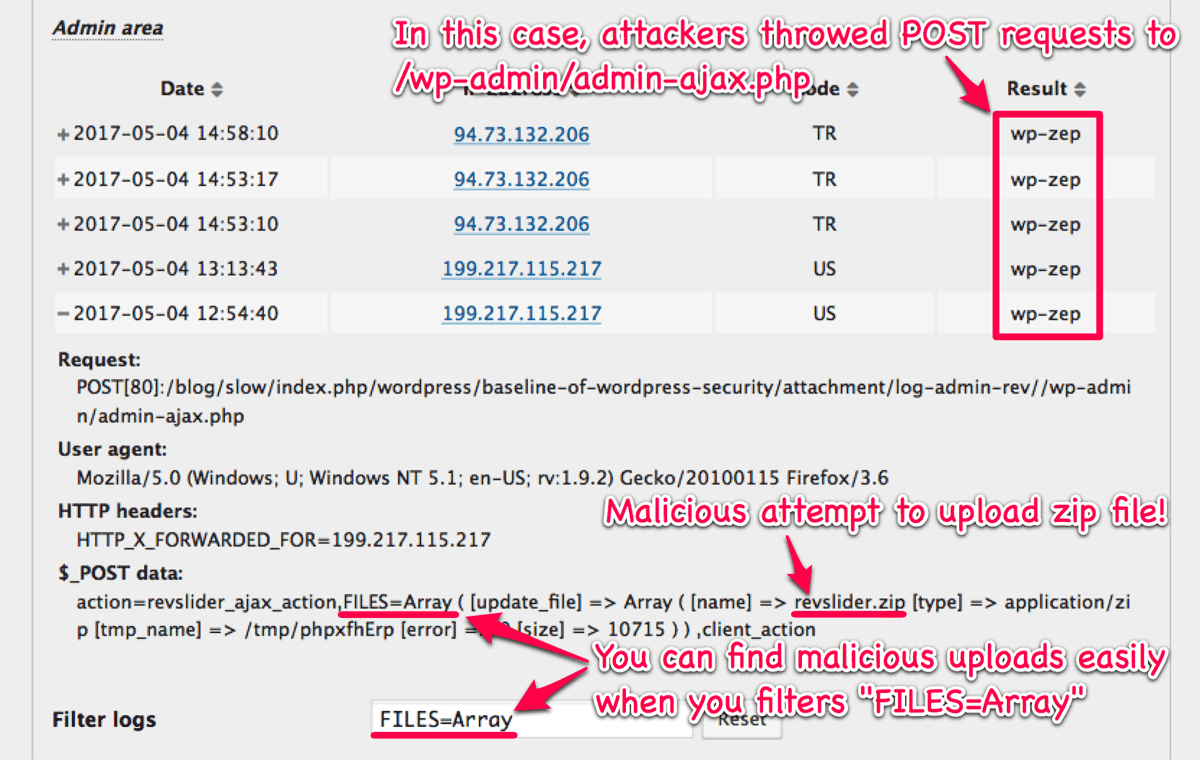
Note that you need to put FILES into “$_POST keys to be recorded with their values in logs” at “Record settings” section to record the content of PHP environment variable $_FILES like the above picture.
New hook: ip-location-block-forbidden-upload
When this plugin detects malicious uploading, the filter hook ip-location-block-forbidden-upload is applied.
I personally utilize it to make the uploaded files immune  from public access and investigate them to study how websites would be exploited
from public access and investigate them to study how websites would be exploited  .
.
If you want to use this feature, do it at your own risk!
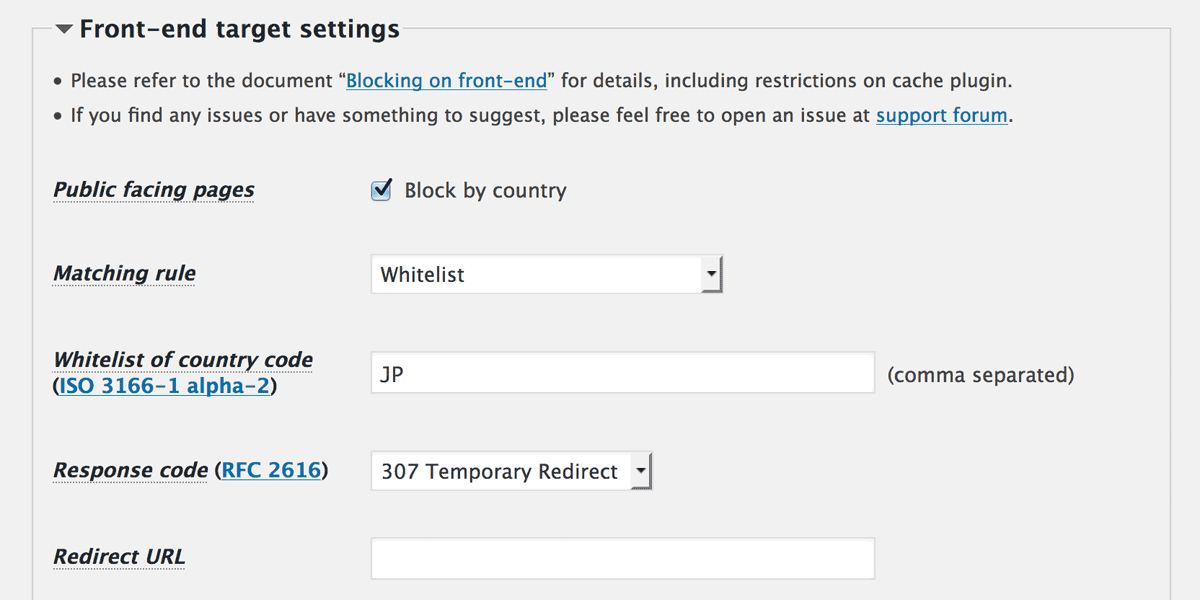
New feature: “Response code” on front-end
From this release, you can configure “Response code” independently on front-end. This is useful not to violate your affiliate program.
Improvement: Enabling/Disabling “DNS reverse lookup”
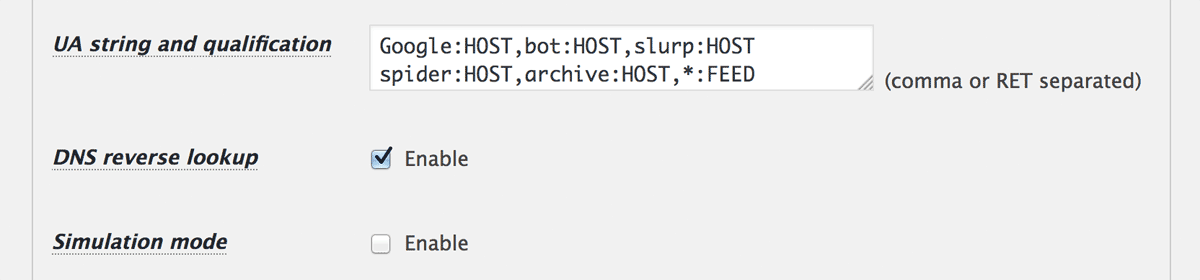
Before this release, if “UA string and qualification” at “Front-end target settings” includes HOST as follows, then DNS reverse lookup would be fetched. This potentially caused 504 Gateway error because the cost of looking up DNS record would be relatively high.
Google:HOST,bot:HOST,slurp:HOST
spider:HOST,archive:HOST,*:FEED
embed.ly:HOST,Twitterbot:US,Facebot:USIf you want to inhibit fetching DNS record, you had to change HOST to * as follows:
Google:*,bot:*,slurp:*
spider:*,archive:*,*:FEED
embed.ly:*,Twitterbot:US,Facebot:USNow you can just check/uncheck “DNS reverse lookup” to enable/disable it.
When it is disabled, then HOST and HOST=... will be converted to *.
Note that *:HOST=yahoo.com or *#HOST=badbot.com for example will be eliminated because those will be turned into *:* or *#* that accepts or blocks all the user agents  .
.

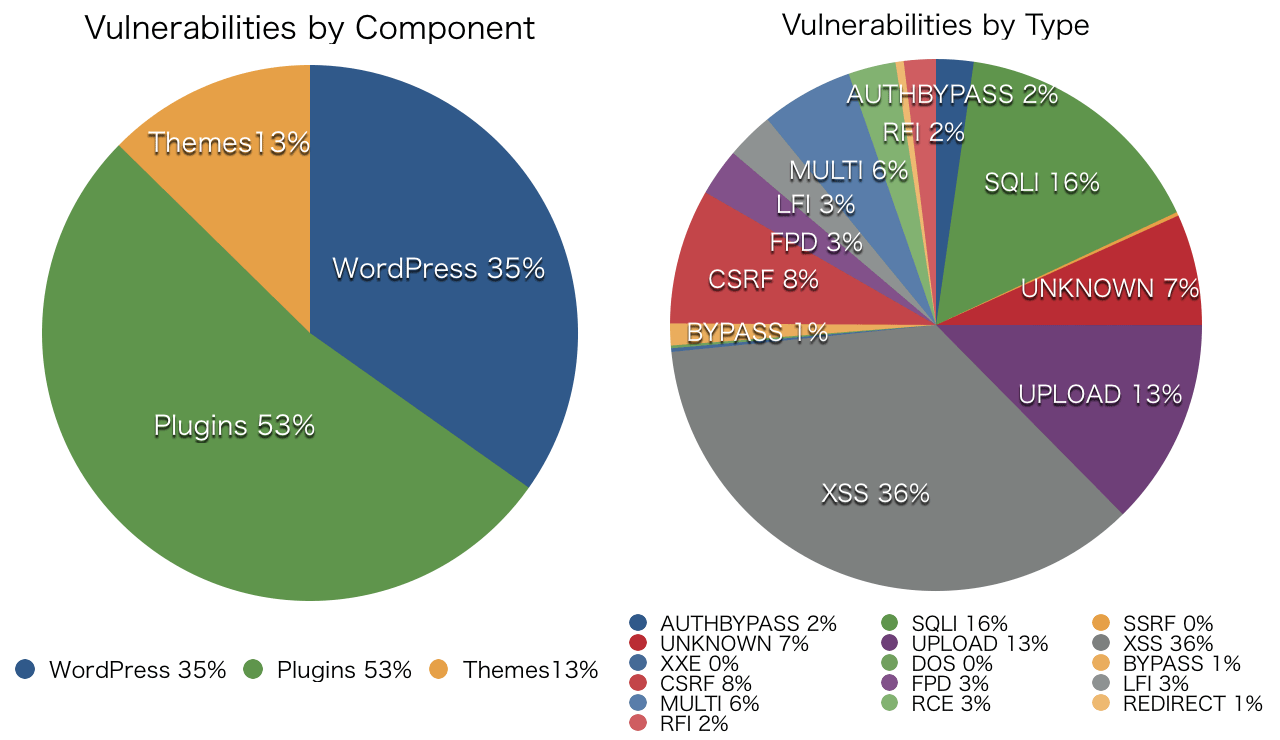 Source: © The WPScan Team
Source: © The WPScan Team