You may want to test the blocking behavior of this plugin. This document shows you how to do it especially arround the admin, plugins and themes area based on version 0.2.2.2 and later.
Preparation
The most easy way to simulate submitting a request from outside of your country is using the browser addon for VPN service.
You can also find many articles that recommend which one is better.
How to test on back-end
After turning on your VPN addon and select the country you need to test, simple visit to your back-end e.g. /wp-login.php, /wp-admin/ or /xmlrpc.php with your browser.
Note that accessing to /xmlrpc.php with browser returns a simple message because this script needs to be accessed by not GET method but POST method.
XML-RPC server accepts POST requests only.
But it doesn’t matter. Your test access would be recorded in Logs tab of IP Location Block dashboard.
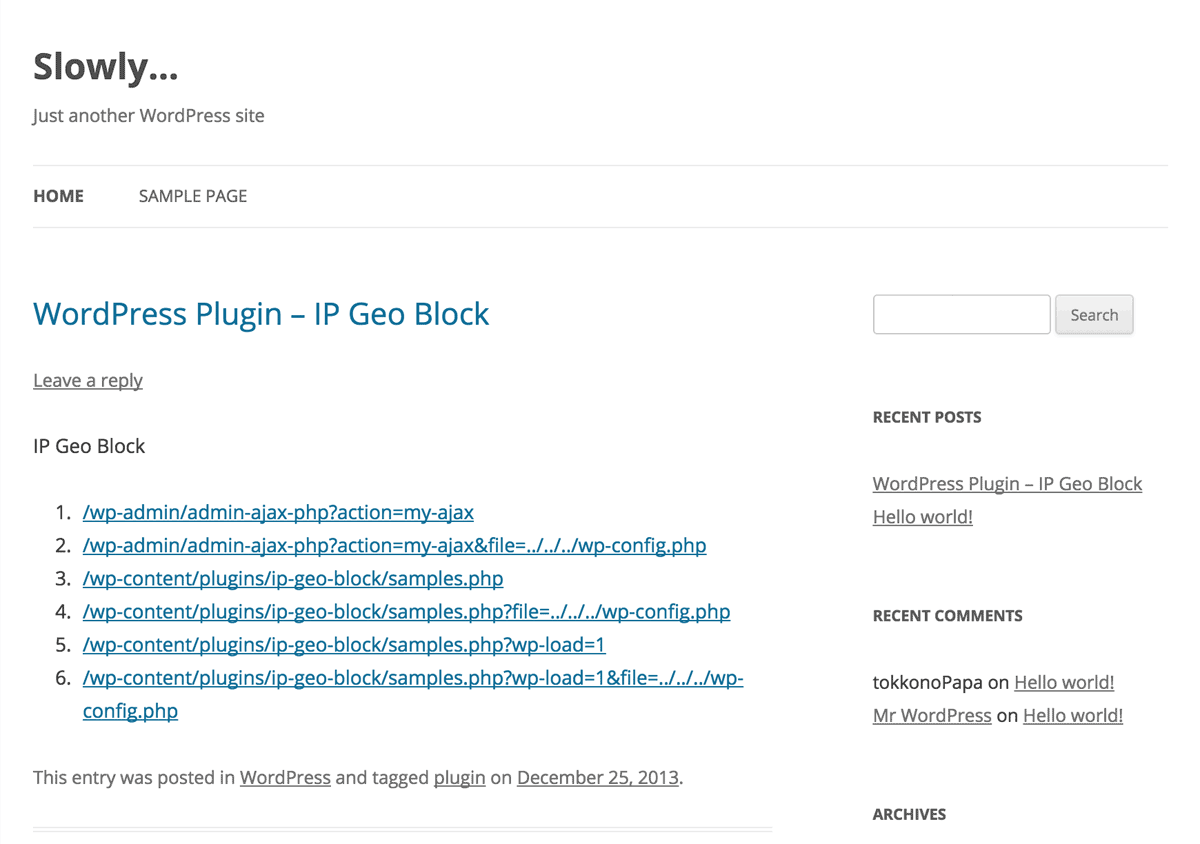
Testing the blocking behavior on Admin ajax/post, Plugins area and Themes area would be a bit complicated. Please submit the following links to your post. The first 2 lines are for admin ajax, and the last 4 lines are for direct access to the PHP file in plugins area. In particular, the last 2 lines will include wp-load.php to load the WordPress core functions.
Ensure that http://example.com is replaced to your WordPress home.
<ol>
<li><a href="http://example.com/wp-admin/admin-ajax.php?action=my-ajax">/wp-admin/admin-ajax-php?action=my-ajax</a>
<li><a href="http://example.com/wp-admin/admin-ajax.php?action=my-ajax&file=../../../wp-config.php">/wp-admin/admin-ajax-php?action=my-ajax&file=../../../wp-config.php</a></li>
<li><a href="http://example.com/wp-content/plugins/ip-location-block/samples.php">/wp-content/plugins/ip-location-block/samples.php</a></li>
<li><a href="http://example.com/wp-content/plugins/ip-location-block/samples.php?file=../../../wp-config.php">/wp-content/plugins/ip-location-block/samples.php?file=../../../wp-config.php</a></li>
<li><a href="http://example.com/wp-content/plugins/ip-location-block/samples.php?wp-load=1">/wp-content/plugins/ip-location-block/samples.php?wp-load=1</a></li>
<li><a href="http://example.com/wp-content/plugins/ip-location-block/samples.php?wp-load=1&file=../../../wp-config.php">/wp-content/plugins/ip-location-block/samples.php?wp-load=1&file=../../../wp-config.php</a></li>
</ol>As you can see, an even line is a malicious request to attempt to expose wp-config.php.
Also to handle a ajax request properly, put the following code into your functions.php.
/**
* Ajax for non privileged user
*
*/
add_action( 'wp_ajax_nopriv_my-ajax', 'my_ajax_handler' );
function my_ajax_handler() {
;
}Blocking malicious request
Now at first, uncheck and disable all the settings for “Admin ajax/post” and “Plugins area”.
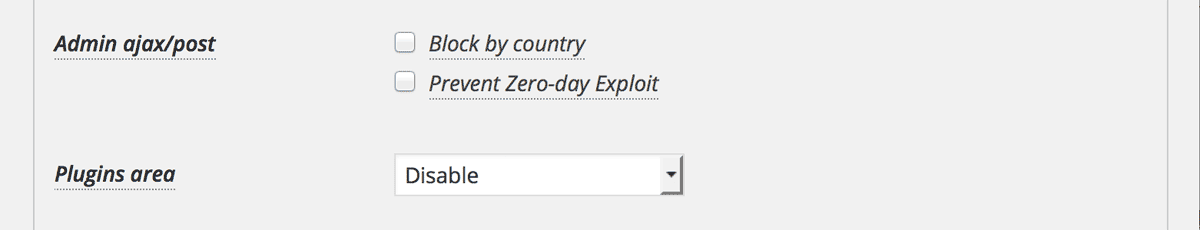
When you assess the above links as a visitor on the public facing page, you’ll see 0 in case your request are success, otherwise you’ll be blocked.
0 (means success), then you should properly configure the `.htaccess` in your plugins area. Please refer to this article. Block by country
OK then, check and enable “Block by country”.
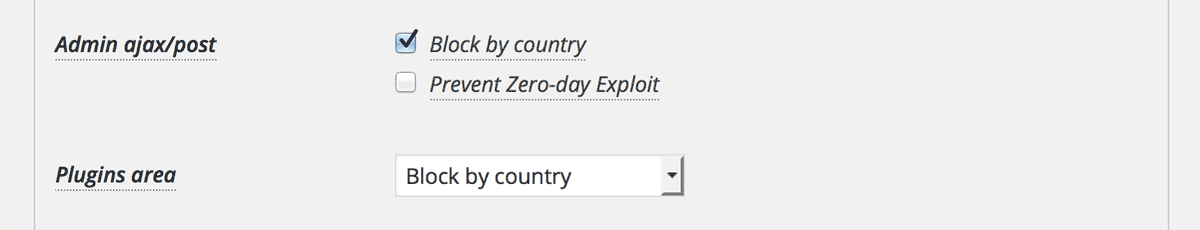
All the links will be blocked when you’re behind the VPN proxy and .htaccess is set properly. And when you turn off the VPN addon, then only the malicious links at even lines will be blocked.
Prevent Zero-day Exploit
Yeah, the last one is “Prevent Zero-day Exploit”.
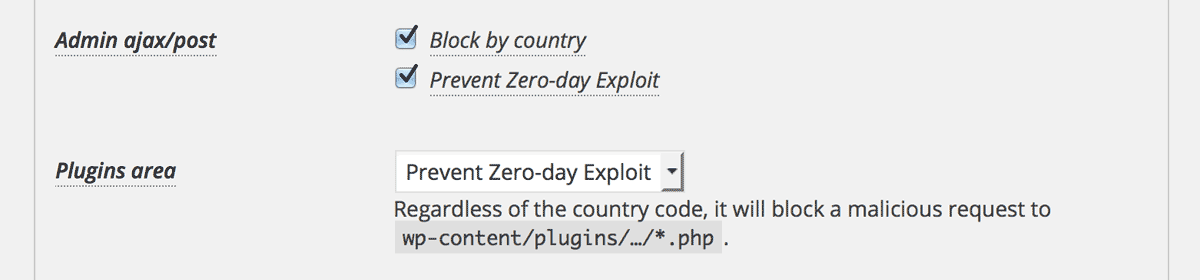
All the links except the 1st one will be blocked. It is because the 1st link is a service for the visitors. If you add the action hook for the admin as follows, then the 1st link is also blocked.
/**
* Ajax for admin
*
*/
add_action( 'wp_ajax_my-ajax', 'my_ajax_admin_handler' );
function my_ajax_admin_handler() {
;
}It means that non privileged user never succeed zero-day attacks via Admin ajax and plugins / themes area. On the other hand, if you’re logged in as an admin, all the links at odd lines will not be blocked.
rel="nofollow" into each anchor tag. In this case, WP-ZEP will block every link to prevent CSRF. 